WHAT IS:-(R.F.I.D)!......
WHAT IS R.F.I.D !........
Radio Frequency Identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a small radio transponder, a radio receiver and a transmitter. When triggered by an interrogating electromagnetic pulse from a nearby RFID reader, the tag sends digital data (usually an identifying inventory number) back to the reader. This number can be used to track inventory items.
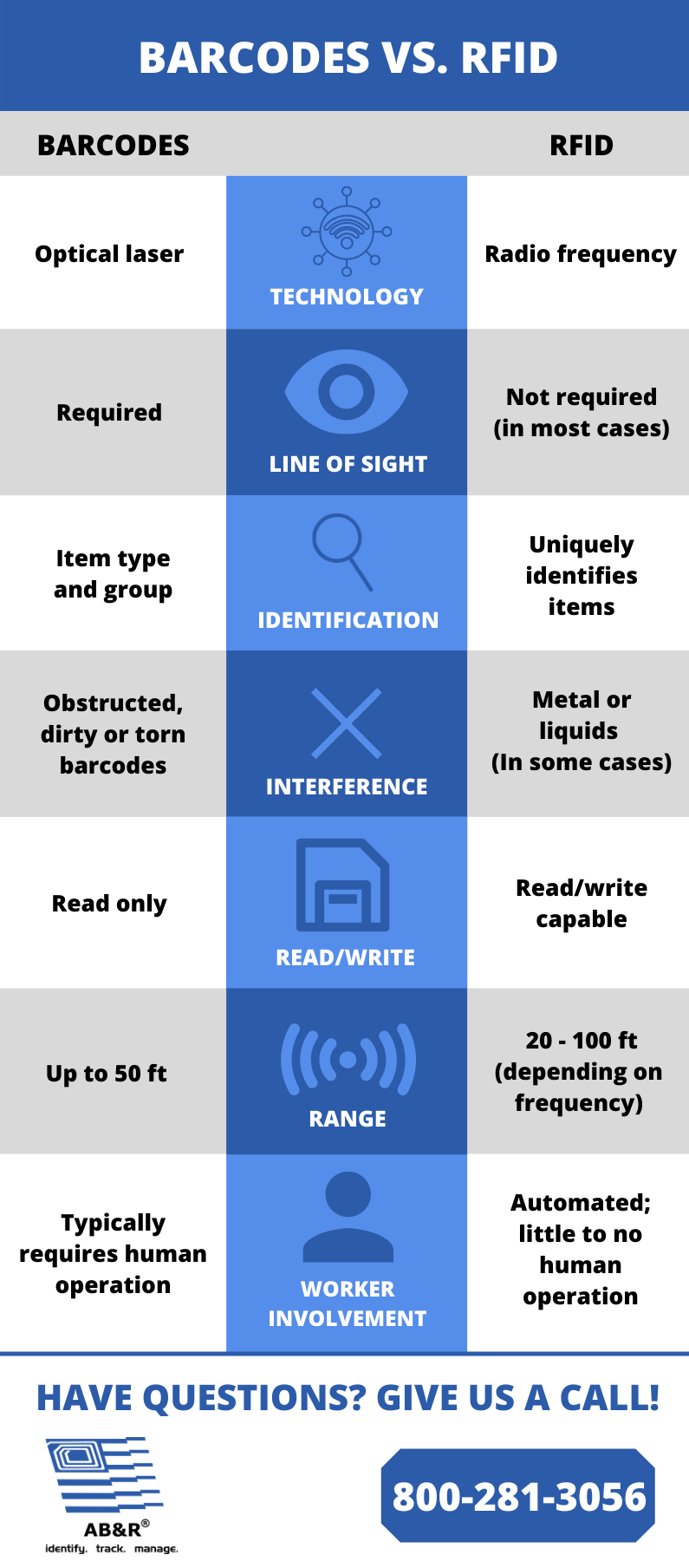
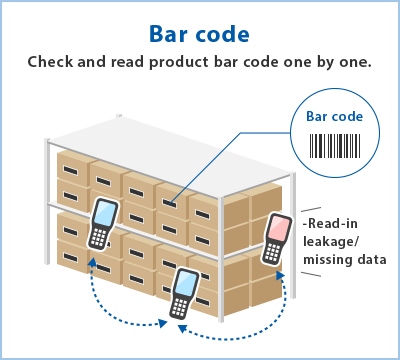
Passive tags are powered by interrogating radio waves from an RFID reader. Active tags are battery powered and can be read by RFID readers from up to hundreds of meters away. Unlike bar codes, labels do not have to be in the reader's field of view, so they can be incorporated into tracked objects. RFID is one method of automatic identification and data collection (AIDC).
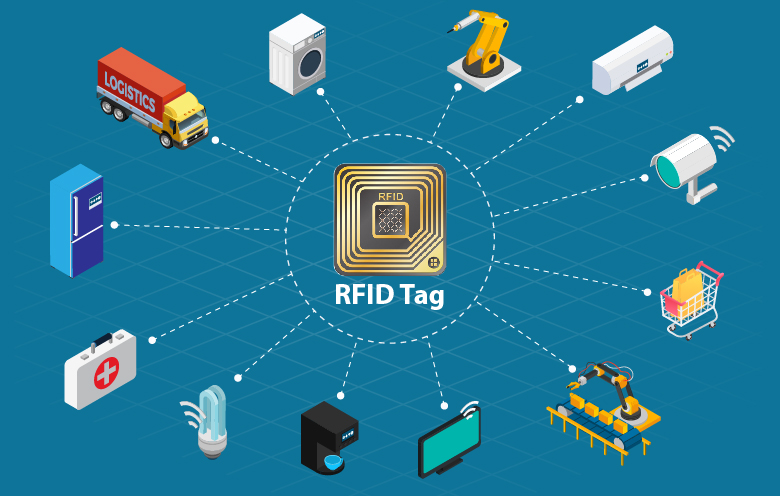
RFID tags are used in many industries. For example, RFID tags attached to cars during production can be used to track assembly line progress, RFID tagged pharmaceuticals can be tracked in warehouses, and RFID microchips can be implanted in livestock and pets to protect animals. Can be uniquely identified. . Tags can also be used in stores to speed checkout and prevent theft from customers and employees. Because RFID tags can be attached to physical money, clothing, property, or embedded in animals and humans, the ability to read personal information without consent raises serious privacy concerns.
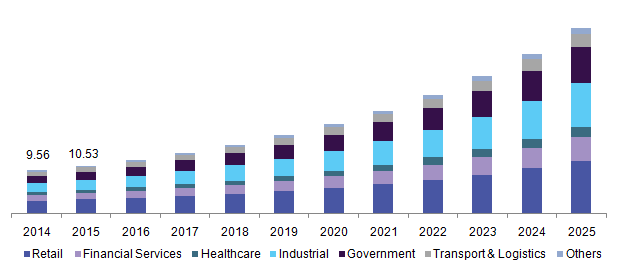
These concerns have led to the development of standards that address privacy and security issues. His RFID market in the world in 2014 increased from US$7 to US$8.89 billion$77 billion in 2013 and $6.96 billion in 2012. This number includes tags, readers and software/services for RFID cards, tags, tags and all other form factors. Market value is expected to increase from $12.08 billion in 2020 to $16.23 billion in 2029. In 1945, Leon Theremin invented the Thing. This is a listening he device for the Soviet Union that transmits incoming radio waves with the addition of audio information. Sound waves vibrated the membrane, slightly changing the shape of the resonator and modulating the reflected radio frequencies. This device, which was more of a covert listening device than an identification tag, is considered the predecessor of RFID.
This is because they are passive and are powered and activated by waves from an external source. Similar technology. B. Transponders for friendly or foe identification were widely used by the Allies and Germany during World War II to identify aircraft as friend or foe. Transponders are still used on most aircraft today. The first paper to look at RFID was a seminal 1948 paper by Harry Stockman, which called it ``before solving the remaining fundamental problems in reflected power communication and making the field more useful. In addition, considerable research and development will have to be done.” Under study." Mario Cardullo's device, patented on January 23, 1973, was
The first true predecessor of his modern RFID, as it is a passive radio transponder with memory. The original device, passive powered by an interrogation signal, was demonstrated to the New York Port Authority and other potential users in 1971. It consisted of a transponder with 16-bit memory for use as a repeater.Cardullo's basic patent covers the use of radio frequency (RF), sound and light as transmission media. The original business plan presented to investors in 1969 showed uses in transportation (automobile vehicle identification, automatic toll system, electronic license plate, electronic manifest, vehicle tracking, vehicle performance monitoring), banking (electronic checkbook, electronic credit card), security (personnel identification, automatic gates, surveillance) and medical (identification, patient history). In 1973, Steven Depp, Alfred Koelle, and Robert Frayman performed the first demonstration of reflected power (modulated backscatter) RFID tags, both passive and semi-passive, at Los Alamos National Laboratory.
The portable system operated at 915 MHz and used 12-bit tags. Most of today's UHFID and microwave RFID tags use this technique. In 1983, Charles Walton received the first patent associated with the acronym RFID. In 1996, the first patent for interference-limited, batteryless, passive RFID tags was granted to David Everett, John Frech, Theodore Wright, and Kelly Rodriguez. Type radio frequency identification systems use tags or tags attached to the object to be identified. A two-way radio transmitter and receiver, called an interrogator or reader, sends a signal to the tag and reads its response. Tag The RFID tag consists of three parts: board. tag information is stored in non-volatile memory. RFID tags can be passive, active, or battery powered. Active tags have a built-in battery and periodically transmit an ID signal. Tags are either read-only, using the factory-assigned serial number as the key in the database, or read-only, which allows system users to write object-specific data to the tag.In practice, programmable tags can be either single-write or multiple-read. The user can enter a "blank" label using the product's electronic code. RFID tags receive messages and respond with their identification and other information. A unique serial number on a label or product-related information such as an inventory number, lot or lot number, date of manufacture, or other specific information. Because tags have individual serial numbers, RFID system designs can distinguish between multiple tags that may be within range of an RFID reader and read them simultaneously. Readers RFID systems can be categorized by tag and reader type. There are 3 types. The Active Tag Passive Reader (PRAT) has a passive reader that only receives radio signals from active tags (battery powered, transmit only).
The range of the PRAT system reader is adjustable from 0 to 600 m (1 to 2,000 ft), providing flexibility for applications such as asset protection and surveillance. Active Reader Passive Tag (ARPT) systems have an active reader that sends a challenge signal and also receives authentication responses from passive tags. The Active Reader Active Tag (ARAT) system uses active tags that are activated by an interrogation signal from an active reader. A variant of this system could be a battery-backed passive tag (BAP) that acts like a passive tag but has a small battery that powers the tag's feedback signal. fixed readers are set up to create specific interrogation zones that can be tightly controlled. This allows for high resolution
Signaling between the Rigid RFID signaling reader and the tag occurs in various incompatible ways depending on the frequency band used by the tag. Tags operating in the LF and HF bands are very close to the reader's antenna on a wavelength and only a fraction of a wavelength away. At this short range, the tag is electrically coupled closely to the transmitter inside the reader. The tag can modulate the field generated by the reader by changing the voltage it generates.
By switching between high and low relative forces, the label creates a change that can be detected by the reader. At frequencies above UHF, tags require a different approach as tags are one or more radio waves away from the reader. Tags can redistribute signals. An active tag can have a functionally separate transmitter and receiver, and the tag does not have to respond on a frequency related to the reader's polling signal. An electronic product code (EPC) is a common type of data stored on labels. When written to a tag by an RFID printer, the tag contains a 96-bit data string. The first 8 bits are a header identifying the protocol version. The next 28 bits identify the organization that controls the data in this tag. Organization numbers are assigned by the EPCGlobal Consortium. The next 24 bits are an object class that identifies the product type. The last 36 bits are the unique serial number of the specific tag.
These last two fields are set by the organization that issued the tag. Like a URL, an integer electronic product number can be used as a key in a global database to uniquely identify a particular product. Often multiple tags respond to the tag reader. For example, many individually tagged products may be shipped in common boxes or common pallets. Collision detection is critical to the ability to read data. Two different types of protocols can be used to "aggregate" a particular tag so that its data can be read across many similar tags. In a slotted Aloha system, the reader sends an initialization command and parameters that the tags use individually, with pseudo-random delays in response.
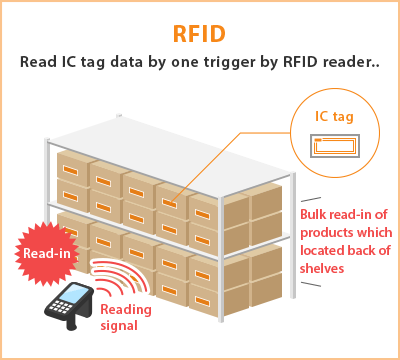
Using the "Adaptive Binary Tree" protocol, the reader sends an initialization symbol, followed by ID data one bit at a time. Only tags with matching bits will respond and in the end he only one tag matches the full id string. Binary Tree Method Example for Identifying RFID Tags Both methods have drawbacks when used with large numbers of tags and multiple duplicate readers. Bulk Read Bulk Read is a strategy to query multiple tags at once, but it is not precise enough for inventory management. A group of objects that are all RFID tagged can be read completely simultaneously at one reader position.
However, tags respond strictly sequentially, so the time required to bulk read increases linearly with the number of tags read. That means reading a label twice as long will take at least twice as long. The impact of collisions increases time consumption. A group of labels should be highlighted by the voting signal as if it were a single label. This is not an energy challenge, it is a visibility challenge. If one of the tags is occluded by another tag, it may not have enough illumination to give a proper response. Although the response conditions of inductively coupled HF RFID tags and coil antennas in electromagnetic fields appear to be superior to those in UHF or SHF dipole fields, distance limitations apply and may hinder their success.
Bulk reads are unreliable under production conditions. And they can be a rough guide for logistics decisions, but they are not yet suitable for [when?] inventory management due to the high rate of read errors. However, if a single RFID tag does not guarantee a good read, using multiple RFID tags with at least one response can provide a more secure approach to detecting known groups of objects.
Increase , in this regard, bulk reading is a fuzzy way to assist the process. From a cost-effectiveness point of view, bulk reading does not appear to be a cost-effective approach to ensuring logistical process control. Miniaturization RFID tags can be easily hidden or integrated into other objects. For example, in 2009 researchers at the University of Bristol successfully attached RFID microtransponders to living ants and studied their behavior. This trend toward increasingly miniaturized RFID is expected to continue as the technology advances. Hitachi holds the record for making the smallest RFID chip at 0.05 x 0.05mm. This compares to previous record holder Mu Chip and is 1/64 his size. It can be produced using the silicon-on-insulator (SOI) process. This dust-sized chip can store 38 digits using 128-bit ROM (read-only memory). The main challenge is mounting the antenna, which limits the read range to just a few millimeters..............
TO BE CONTINUED WITH
A R D U I N O









Comments
Post a Comment